What’s happening
All large and not very corporations cooperate with law enforcement agencies, subject to the laws of the countries in which they work. Google, Apple, Facebook, Skype, WhatsApp, Viber and many other social networks and instant messengers are sharing with the authorities some amount of user data. Someone merges more, some less, but the bitter truth is that everyone does it.
Demonstrative fighters for freedom without batting an eye will give out all your secrets. For example, the creators of the popular Viber messenger, who, according to Russian legislation, were ordered to move servers to the territory of the Russian Federation, complied with the authorities’ demands at the end of last year. Officially, this step is explained by the need to store personal data on servers inside the country, but we all know the true motives: it’s the desire of special services to get access to correspondence.
Familiar operatives reported a vesh that I had long expected – any correspondence on Viber they get even easier than typing SMSok.
Published by Alexander Kovalenko on March 1, 2016.
By “easier” in this case, it means that for surveillance, even interaction with cellular network operators is not required: all the necessary tools are available to the relevant authorities. The same applies to WhatsApp, Skype and other messengers, not to mention ordinary SMS. Moreover, not only special services can read your correspondence, but also competitors, enemies and anyone else who can use the services of special services. They are cheap and easy to google on request “print SMS”.
When law enforcement agencies can not obtain the data they need with the help of existing levers of pressure, they take radical measures. Literally in early March, the vice-president of the Latin American branch of Facebook was detained for refusing to cooperate with the Brazilian police. The subject of disputes was information about users of social networks, allegedly involved in the distribution of drugs.
In December 2015, the Brazilian court blocked WhatsApp (owned by Facebook) on the territory of the country after refusing to provide information about the correspondence of the alleged criminals. In the end, all suffered: the police disconnected about 100 million local users, triggering a violent reaction in social networks and the indignation of Facebook CEO Mark Zuckerberg (Mark Zuckerberg).
Even more revealing in the struggle for the inviolability of personal data is the confrontation between Apple and the FBI, which so far has not received its denouement. Special services say about preventing terrorist attacks and ensuring national security, not wanting to admit that in this way crime can not be defeated. Apple’s chief legal counsel at congressional hearings said that even if the special services had the opportunity to crack any iPhone, criminals would in any case have found ways of secret communication, and cited Telegram as an example.
Against scrap there is a reception
The representative of Apple is right: there are a lot of ways of secure correspondence and they were invented far from yesterday. The brainchild of Pavel Durov Telegram is the first to come to mind because of its popularity and unblemished reputation: a reward of $ 200,000 awarded back in 2013 for hacking encrypted telegram correspondence has not yet been received.
Such invulnerability is explained by the very principle of the work of the protected instant messengers in general and Telegram in particular. The latter uses a specially developed MTProto protocol and two-layer encryption with 256-bit AES-key: they provide high speed and reliability. And in Telegram, in addition to the usual chat rooms, there are so-called Secret Chats. In them, the correspondence is encrypted without the participation of the server, and all messages are sent directly from the sender device to the recipient device (peer-to-peer). Even if we assume that data can be intercepted, it will be impossible to decipher them without the keys stored on the devices of the participants in the conversation.
Another advantage of P2P-transmission is that the messenger’s work can not be blocked: when there are no servers, there simply is not enough to block.
Governments of authoritarian countries often sin by blocking unwanted services. For example, everyone knows about Facebook, which is blocked almost all over China. In October last year, due to the refusal to provide an opportunity for surveillance of Telegram users, it was partially partially, and then completely blocked in Iran. You can avoid such situations with the help of P2P communication, which Pavel Durov promised to implement after this incident.
@emmanuelksvz We are working on a P2P solution that will make the service unblockable. It’ll take some time.
– Pavel Durov (@durov) October 20, 2015
A similar approach is used in various secure instant messengers with end-to-end encryption. The method of transferring the keys may be different, but the principle remains unchanged: the information is sent directly from the device to the device without the participation of intermediate servers.
Something like that, probably, will soon appear in Facebook Messenger. Journalists edition of The Information dug in the code of the iOS-application rather curious comments. They point to an analog of Apple Pay, allowing you to pay for goods and send money to users, as well as the associated functionality of secret chat rooms. The way to implement such conversations is still difficult to judge: Facebook can follow the path of Telegram and implement encryption, or can simply add the ability to hide individual correspondence and contacts. In any case, even if the decision is made in favor of the first option, attract users and prove to them that the secret chats in the Messenger are really safe, it will not be so easy.
How to be
To those for whom the reliability of the communication channel plays an important role, it is worth paying attention to the secure messengers with the mentioned encryption. They will suit not only paranoiacs, but also all those who are connected with business and have access to any more or less important information that is not intended for other people’s eyes. There are a lot of affordable solutions, but we will not consider them all, but we will stop at the three most convenient ones.
Secret Chats Telegram
Thanks to the wide distribution of instant messenger, secret telegrams can be called ideal. They guarantee the security of sent information, have the function of self-destructing messages (including photos and files) after a certain time and do not allow forwarding correspondence to other people. For greater security with one user, you can create several conversations and discuss various topics in them.
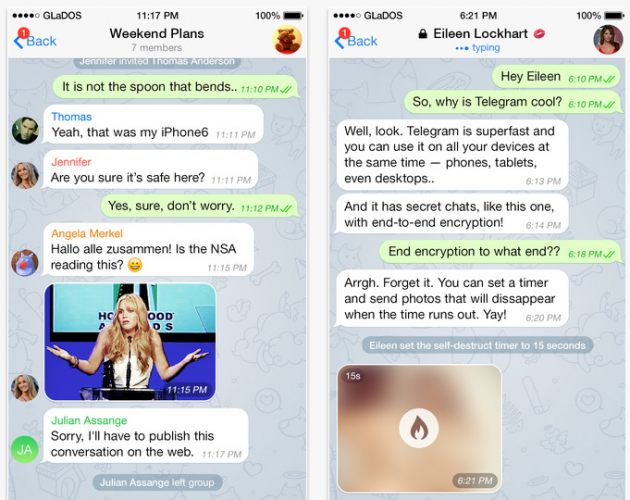
To create a secret chat simply: click the New Message → New Secret Chat icon and select the desired contact. You can start correspondence as soon as a person appears on the web. Due to the lack of intermediate servers, you can not send a message offline. In this case, all unsent messages are stored only on your device. To understand that the chat is secret, but not regular, you can click on the lock icon next to the contact’s name.
Download Telegram (for free) →
Confide
Unlike Telegram, Confide is initially sharpened for maximum security. The messenger is also quite popular in its niche, it is free and has customers for all desktop and mobile platforms. Confide uses end-to-end encryption and does not store messages anywhere except the sender and receiver devices. Moreover, the messenger does not even display the text of the received message entirely, but breaks it into blocks and shows it in parts when you move your cursor or touch with your finger. The read messages are immediately deleted. Those who want to save the content using the screenshot will expect a failure: the text will instantly be deleted, and the sender will receive a notification of the failed attempt of the interlocutor.
The account in Confide is attached to the email, after registration you can connect your social networks and allow access to contacts. If someone from your friends has an application installed, you can safely correspond, send photos and documents.
Download Confide (free) →
Threema
And this application is already for real paranoiacs. It is paid, not so convenient, has a less friendly interface, but is even more rotated by security and works only with direct encryption. No phone number or email is used here. Threema requires a pair of keys that you will generate at the first start: one of them is private and stored on your device, the other is public and sent to your interlocutor. After that, you will be assigned an identifier, by which you can be found. You can add a contact either by email or by phone (if the person has tied them to the account), and also by scanning the QR code in person (this is the safest option).
Threema allows you to exchange not only text messages, but also photos, videos, documents and geoms. There are applications for iOS, Android and Windows Phone.
Download Threema (from 129 rubles) →
Signal
Signal recommends Edward Snowden himself (Edward Snowden), which in itself already means something. Like the previous ones, this application uses end-to-end encryption, but differs in that besides sending text messages, photos and files, it also supports voice calls. Signal is attached to your phone number and allows you to safely communicate with contacts from your phone book. On Android, you can even make it the default app for making calls and sending messages. Recently, Signal has become available on desktops as a Chrome-based application.
Download Signal →
And what do you think about protected instant messengers: is it worth to go over to them or is it just for paranoiacs? Tell us if you use secure chat rooms, and if so, which ones have been preferred and why.
